Open Raven Blog
Freeform, live sessions focused on recent events and trends in data and cloud security.
Filter by:
Clear all
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Discover and Classify Data

Discover and Classify Data
Operationalizing Data Security in the Cloud at Scale - Data Classification Explained Part 3
March 8, 2024
Read more
Release Notes

Release Notes
Open Raven Platform Release: SaaS Data Loss Prevention for Google Drive
December 29, 2023
Read more
Company
Enforce Policies for File and Folder Sharing
Streamline Offboarding of People and Partners

Company
Modern Data Security Still Needs (a Different Type of) DLP
December 11, 2023
Read more
Eliminate Shadow and Stale Data

Eliminate Shadow and Stale Data
Introduction to Stale Data
July 25, 2023
Read more
Discover and Classify Data

Discover and Classify Data
Operationalizing Data Security in the Cloud at Scale - Data Classification Explained Part 2
July 25, 2023
Read more
Assess the Security Posture of Data

Assess the Security Posture of Data
How Open Raven Complements CSPMs - Real World Examples
June 22, 2023
Read more
Discover and Classify Data

Discover and Classify Data
Transforming Data Classification Testing with Generative AI
June 5, 2023
Read more
Discover and Classify Data

Discover and Classify Data
Operationalizing Data Security in the Cloud at Scale - Data Classification Explained Part 1
May 25, 2023
Read more
Discover and Classify Data

Discover and Classify Data
Structured Cloud Data Discovery & Classification: What You Should Know About Snapshot Scanning
April 25, 2023
Read more
Discover and Classify Data

Discover and Classify Data
Enterprises Prioritize Data Classification in 2023
April 14, 2023
Read more
Prevent Data-Focused Attacks

Prevent Data-Focused Attacks
Speeding Investigations and Uncovering Risky Misconfigurations Using Maps
February 13, 2023
Read more
Establish Guardrails for Data

Establish Guardrails for Data
HITRUST & Data Security - Part 3 of 3
January 25, 2023
Read more
Assess the Security Posture of Data

Assess the Security Posture of Data
Platform Enhancements for Structured Data Scanning
December 20, 2022
Read more
Assess the Security Posture of Data

Assess the Security Posture of Data
Why Customization is Critical for Previewing Sensitive Data Findings
December 20, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
HITRUST & Data Security - Part 2 of 3
December 6, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
HITRUST & Data Security - A Three Part Series
November 8, 2022
Read more
Discover and Classify Data

Discover and Classify Data
Safe and Private Cloud Data Classification Without Backhauling
October 19, 2022
Read more
Discover and Classify Data

Discover and Classify Data
Sampling Unstructured Data Brings Risk of Silent Failure
October 19, 2022
Read more
Discover and Classify Data

Discover and Classify Data
Achieving Complete and Accurate Data Scans Using Validator Functions
September 9, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
Engineering Effective Data Security Alerts - Data Security Rules Explained Part 4
August 19, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
How to Use Data Context to Ensure Compliance - Data Security Rules Explained Part 3
August 5, 2022
Read more
Prevent Data-Focused Attacks

Prevent Data-Focused Attacks
Analyzing the Travis CI Attack and Exposure of Developer Secrets
June 24, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
Types of Data Security Risks - Data Security Rules Explained Part 2
June 10, 2022
Read more
Discover and Classify Data

Discover and Classify Data
Scanning for Developer Secrets in Git Repositories using Open Raven
June 1, 2022
Read more
Prevent Data-Focused Attacks

Prevent Data-Focused Attacks
How Threat Actors Steal Developer Secrets
May 24, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
Operationalizing Data Security in the Cloud at Scale - Data Security Rules Explained Part 1
May 17, 2022
Read more
Assess the Security Posture of Data

Assess the Security Posture of Data
The Dangers of Exposed Elasticsearch Instances
March 11, 2022
Read more
Establish Guardrails for Data

Establish Guardrails for Data
Using Lambda in AWS? There’s Something You Should Know About VPC NAT Timeouts
December 19, 2021
Read more
Prevent Data-Focused Attacks
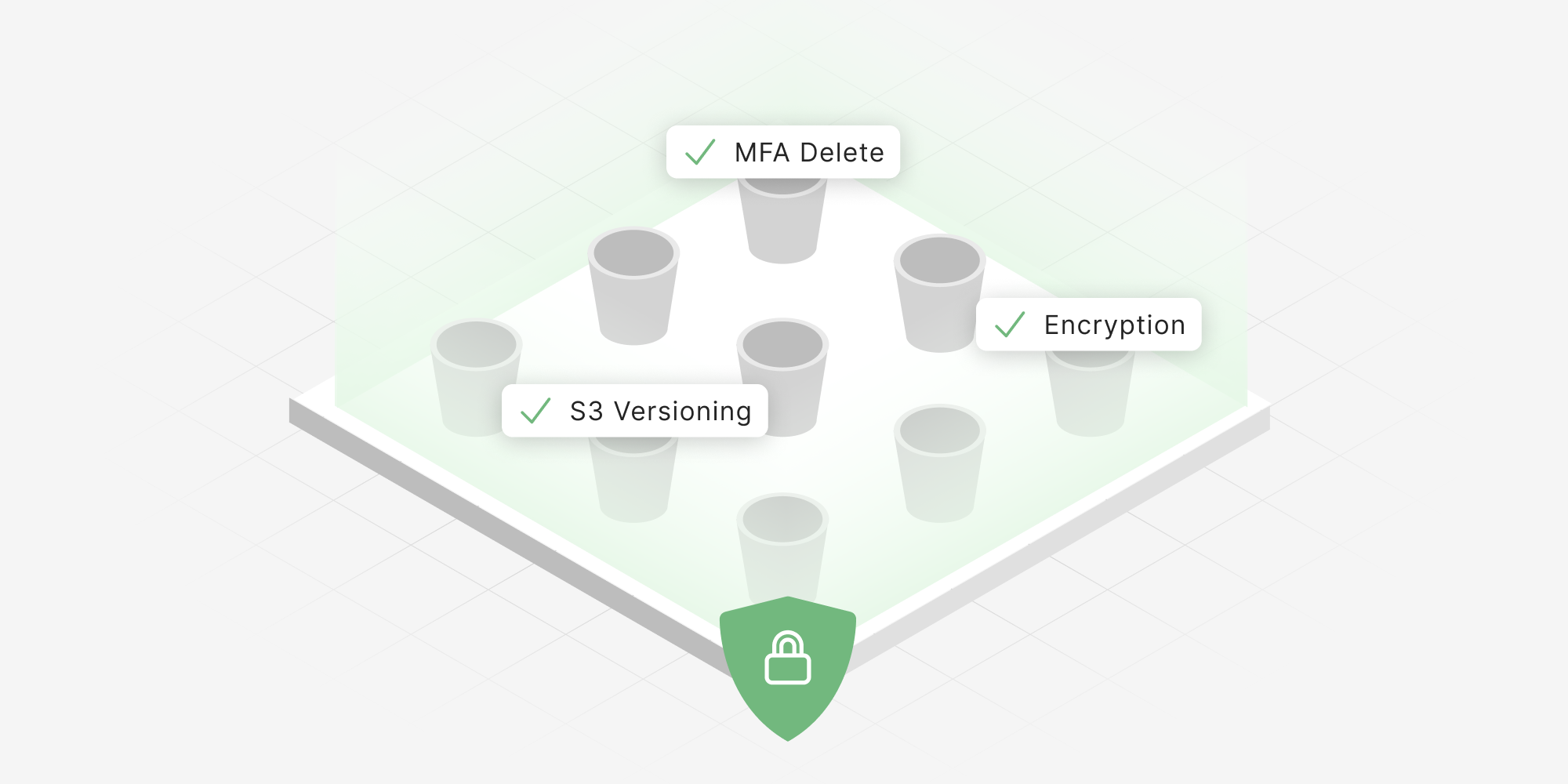
Prevent Data-Focused Attacks
3 Critical Controls for Protecting Data from Ransomware Attacks in AWS
November 15, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: Auto-Scan, Speed & Scale
November 3, 2021
Read more
Prevent Data-Focused Attacks
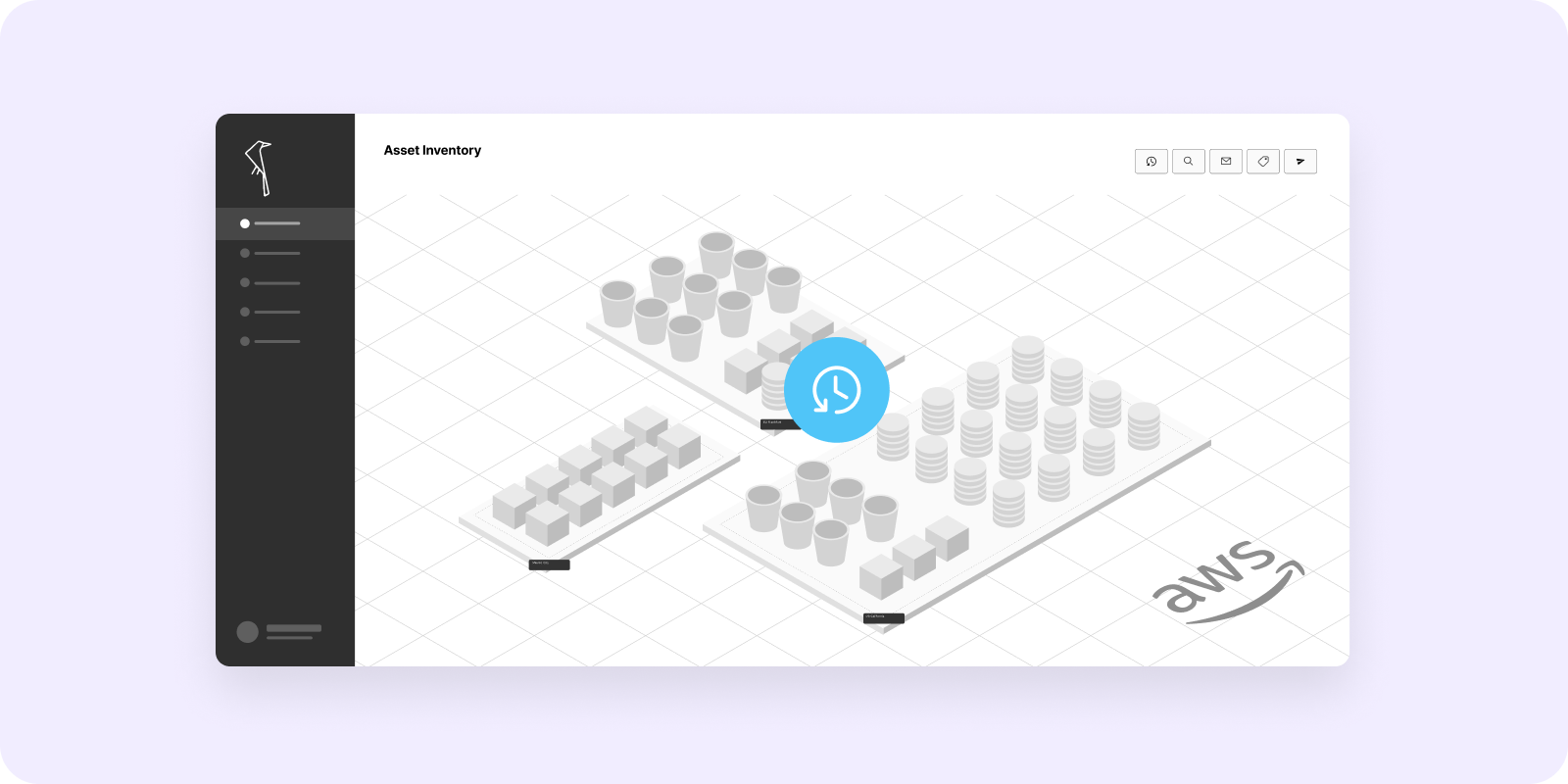
Prevent Data-Focused Attacks
4 Steps to Secure Your Data with AWS Backup and Open Raven
October 28, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Finding Sensitive Data in Cold AWS S3 Buckets
October 13, 2021
Read more
Company

Company
Open Raven Summer 2021 Product Launch: Master Ransomware Resilience
September 2, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: Dashboards and Search with Integrated Splunk
August 26, 2021
Read more
Establish Guardrails for Data

Establish Guardrails for Data
Audit and Report on Data Privacy
August 26, 2021
Read more
Prevent Data-Focused Attacks

Prevent Data-Focused Attacks
Blue Team Diaries: Becoming Data Smart
August 11, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: A Data-Smart Map of Your Cloud
August 10, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Automate Cloud Data and Asset Inventory
August 4, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Automate Data Classification to Combat Secret Sprawl
July 27, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: One-Click Preview of Data Findings
July 26, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Find and Act on Exposed Data
July 7, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Open Raven vs Macie: Healthcare Data Results - Part 5
June 2, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: Policy Violations When Data Is the Endpoint
May 28, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Data Classification Techniques
May 19, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Open Raven vs Macie: Financial Data Results - Part 4
May 18, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Navigate Leaky S3 Buckets with Maps
May 6, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: Classification and Account Management
April 28, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Open Raven vs Macie: Performing the Benchmarking - Part 3
April 27, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Searching for and Opening Files in AWS S3 Buckets - Part 5 of 5
April 23, 2021
Read more
Company

Company
Magpie Cookbook #2: Discover and Portscan Your Public EC2 Instances
April 14, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Signal vs Noise - The Cycle of Innovation in Data Classification - Part 4 of 5
April 8, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Using Terraform to Setup Open Raven and AWS Discovery
April 7, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Open Raven vs Macie: Getting the Data for Benchmarking - Part 2
April 6, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Open Raven vs Macie: Data Classification Benchmarking - Part 1
April 1, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Finding and Determining What Data To Classify - Part 3 of 5
March 29, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: Streamlined AWS S3 Data Classification
March 12, 2021
Read more
Eliminate Shadow and Stale Data

Eliminate Shadow and Stale Data
Toxic (Log) Containment
March 4, 2021
Read more
Discover and Classify Data

Discover and Classify Data
Data Warehouses, Data Lakes, Data Lakehouses and the Data Engineering Landscape - Part 2 of 5
February 23, 2021
Read more
Release Notes

Release Notes
Open Raven Platform Release: New Integrations, Parquet & Avro Support, and More
January 14, 2021
Read more
Release Notes

Release Notes
GA Release of the Open Raven Cloud-Native Data Protection Platform 1.0
November 18, 2020
Read more
Prevent Data-Focused Attacks

Prevent Data-Focused Attacks
To Stop Cloud Data Breaches, Find and Fix Cloud Data Misconfigurations
October 28, 2020
Read more
Release Notes

Release Notes
Open Raven Platform 0.9 and a Few Release Updates
October 27, 2020
Read more
Release Notes

Release Notes
Open Raven Platform 0.8 and a Few Related Updates
October 20, 2020
Read more
Establish Guardrails for Data

Establish Guardrails for Data
Cloud Data Stores and Compliance: What’s to Know
August 11, 2020
Read more
Discover and Classify Data

Discover and Classify Data
How to Accelerate Data Migration to Cloud Native Stores
July 21, 2020
Read more

































