Open Raven Summer 2021 Product Launch: Master Ransomware Resilience

Proactively eliminate gaps in ransomware preparedness with unified infrastructure, backup and data-intelligence
Earlier this year, it became clear that our mission to provide security and cloud teams with the visibility and control over their cloud data was well in line with a specific, critical initiative for many organizations: strengthening ransomware resilience. However, much of the prep work needed to successfully recover from a ransomware attack is manual and time-consuming and involves far too many products.
In thinking through how we might be able to help, our focus turned to the time-driven nature of a recovery itself. Simply put, how an organization responds to an attack can be thought of as a classic race against the clock. Organizations need the ability to recover from attacks faster than the time it would take to recover by simply paying the attackers the ransom—payment is not an immediate recovery, either.
The visual below shows the failure state where it makes more sense to pay the ransom than it does to try and recover. If downtime related expenses ($$$$$) exceed the ransom ($$$), or the amount a cyber insurance policy will negotiate and cover for the victim organization, then paying may be the most affordable option. But even as a sensible decision, paying the attackers feels terrible and only serves to further fuel the ransomware economy.

In contrast, if recovery of critical systems and data can be done before related costs would drive a decision to pay the ransom, then the battle against the clock, and the attackers, is essentially won. Recovery preparation minimizes costs ($) that are far less expensive than paying the ransom ($$$). This scenario is what happens with good, ransomware resilience. Your fate is in your own hands, you brush yourself off and move on.

If being able to recover quickly seems obvious, why can’t more organizations do it? Because it’s hard. Certainly more difficult than buying a cyber insurance policy. It requires having an up-to-date knowledge of critical data and resources — the ones that will be targeted. The same resources must be thoughtfully hardened and backed up. And the backups, also a common target, need to be made ransomware resistant as well. Lastly, the ability to recover needs to be timed and tested. Undoubtedly, the amount of work involved, and likely by some of the most skilled people in an organization, has kept many organizations from pursuing an aggressive resilience strategy such as this.
We’ve been working hard the past few months to make undertaking a recovery-focused strategy achievable for the cloud.
Here are the highlights of our Summer Release.
A Map of Your Cloud with Data Labels & Backup Statuses
Open Raven’s mapping and classification functions provide teams with an up-to-date cloud asset and data inventory that can be viewed in a list view, as raw data via query or in our interactive map. Most recently, we’ve added new filters and actions to the Map in order to quickly: see where sensitive data has been found, see which resources have backups enabled, click-through to see additional details such as encryption status, recent backup job summaries and data inventory details. All of this saves precious time for both cursory and specific investigations into the status of an infrastructure’s resilience to threats targeting data.

Seamless Integration with AWS Backup
The key to ransomware resilience is quick recovery of critical assets and data. When designing a backup solution, the challenge is ensuring that backups continue to cover all critical assets and data as the environment changes. Mix in the speed and sprawl of cloud infrastructure, and it’s even more difficult.
“Today’s ransomware responses leave substantial room for improved planning and coordination,” said Nancy Wang, General Manager of AWS Backup and Data Protection. “Organizations regularly pay tens of millions of dollars in ransom to criminals to get their businesses back up and running. With AWS Backup and Open Raven, you can ensure that all your data is backed up in the event of an attack. At the first sign of a threat, you can restore your data immediately, starting with your most business-critical, time-sensitive data stores. AWS Backup and Open Raven bring ransomware readiness, response, and remediation fully under your control.”
By creating a hands-free integration with AWS Backup, we’ve simplified the ongoing management of backups by showing what’s protected, what’s not, and allowing the addition of assets to backup plans directly from the Open Raven ‘Maps’ or the ‘Assets’ list view.

Rules for Hardening
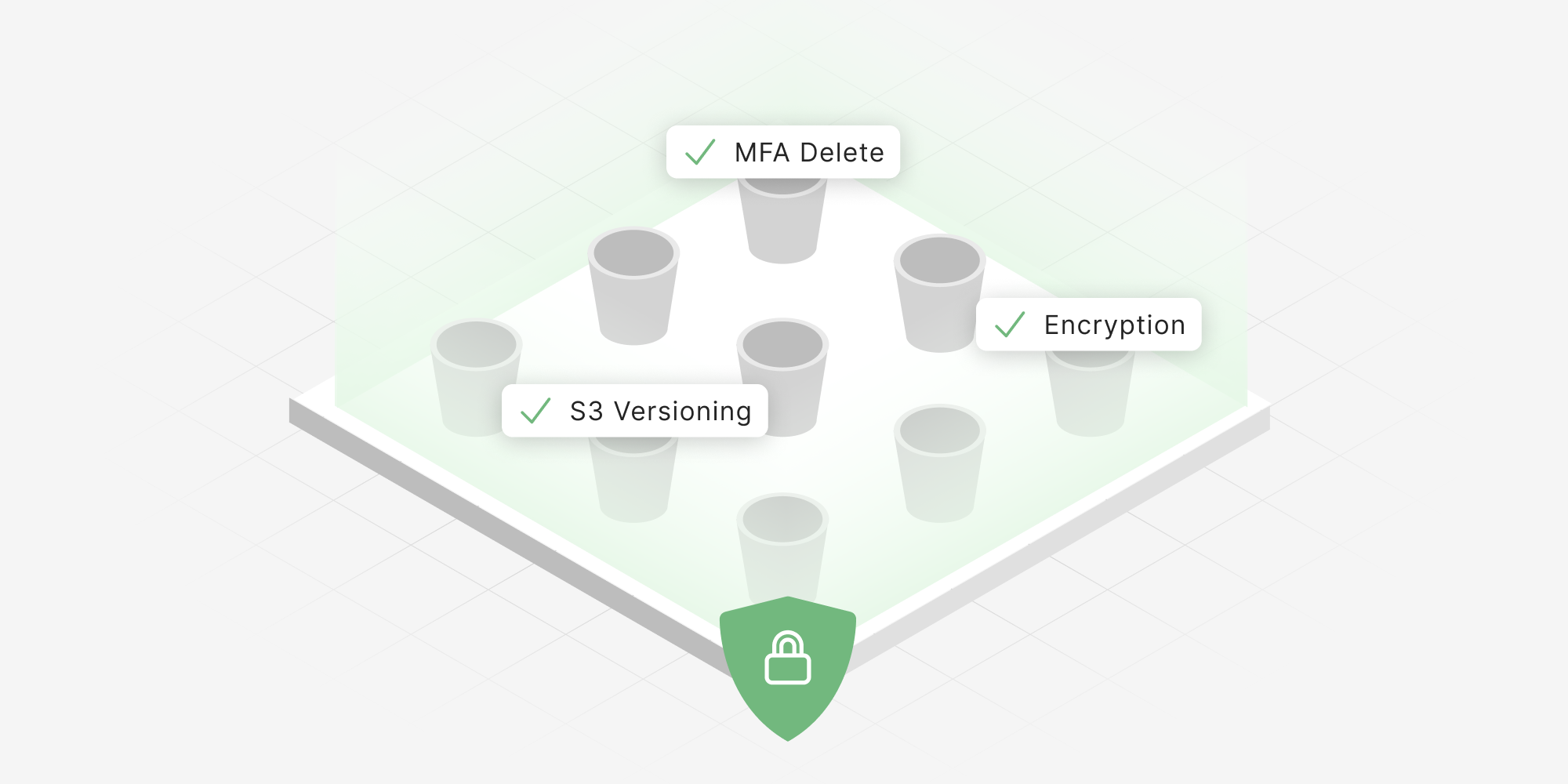
Locking down infrastructure, data and backups is time-consuming work that often requires specialized skills. Further, posture drift is inevitable and ultimately leads organizations to routine assessment, pre-flight checks or even continuous monitoring. In order to ease the burden of knowing what to do and how to do it, we’ve created a series of rules and specific ransomware hardening policies. Specifically, we’ve added rules to alert when resources are particularly susceptible to a ransomware attack, recovery from one, or show indicators of potential compromise. A few examples:
- MFA delete requires multi-factor authentication to perform a deletion of data, helpful in preventing malicious data loss.
- S3 bucket versioning is a policy to ensure that buckets can be rolled back to previous states, extremely useful in the event of malware intrusion like ransomware.
- AWS KMS encryption policies help ensure that attackers that have compromised admin credentials are blocked from decrypting data by not having access to the decryption key.
- And more...
For more information visit our website or schedule a demo to see it in action for yourself. A million thanks to all of our customers, advisors and our friends at the AWS Backup and Data Protection team for helping us with this launch!