3 Critical Controls for Protecting Data from Ransomware Attacks in AWS
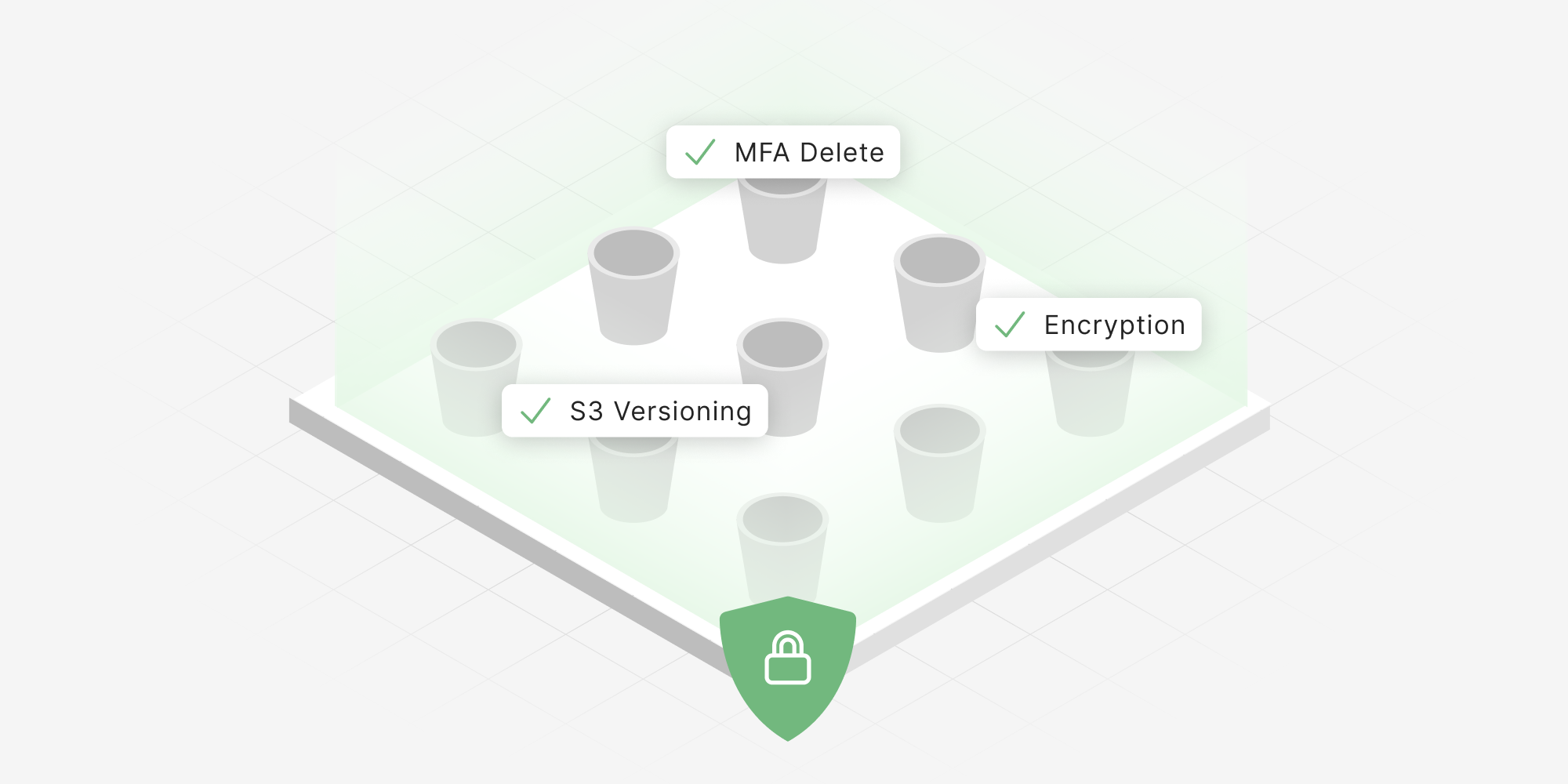
S3 Encryption, Versioning, and MFA Delete are essential for ransomware resilience.
We’re familiar with configuring security policies for networks and applications, but why would you also configure them for data? First, because data is what attackers are after. Second, because the movement of data in the cloud means we must be more direct in our approach as compared with on-premises infrastructure. Historically, data was far less mobile, more or less staying where we expected and designed it to be. In the cloud, data ebbs and flows at speeds, volumes, and varieties that on-premises solutions simply aren’t designed to address, increasing the risk of data breaches and leaks. Open Raven is a cloud-native data security platform designed to make data-centric policies easy for teams to enact.
In just a few clicks, security teams can automatically enforce security controls for specific data types, regardless of location. This allows security teams to configure data guardrails that don’t slow down other parts of the business. While the platform boasts over 150 default rules, we’ll focus on enforcing S3 Bucket Encryption, Versioning, and MFA Delete.
S3 Encryption, Versioning, and MFA Delete
As we’ve written about in a recent eBook, A Guide to Ransomware Resilience, Encryption At Rest, S3 Versioning, and MFA Delete are three effective controls in minimizing the impact and likelihood of ransomware attacks (in addition to good backups). If ransomware attackers can't access or delete your data, then you have achieved a good level of resilience against such attacks. Here's what the controls mean:
S3 Bucket Versioning keeps multiple versions of an object in the same bucket. This means you will be able to revert to versions of your files before they were deleted or changed, almost wholly eliminating the need to pay for decryption keys to regain access to your data.
MFA Delete is a setting that requires (1) user security credentials and (2) a valid serial number, a space, and the six-digit code displayed on an approved authentication device in any request to delete an object or to change the versioning state of a bucket. Such a control is a simple yet powerful way to prevent one of the primary pains caused by ransomware, data loss.
Encryption at Rest means that requests to Amazon will encrypt your objects before saving them on disks in its data centers, and will decrypt when you download the objects. This significantly reduces risks of doxxing and theft since attackers would first need to decrypt the data for it to be valuable in either case (Note: there are other rules to consider to contain breaches of admin accounts).
We've taken these controls, plus hundreds of others, and made them available as default rules that can be quickly enabled out-of-the-box. Here's how it works:
Step 1. Initial Setup and Configuration
First, connect your cloud to the Open Raven platform. Doing so requires an AWS account with a dedicated IAM role and read-only access to your cloud. Connections can also be made manually via CloudFormation or Terraform. Once verified, Open Raven will auto-discover and map all cloud assets, populating Maps and the Asset List. After the discovery has run, create a new auto-scan job by navigating to the Scans menu item and selecting “Create New Auto-scan Job”. This will begin identifying sensitive data types stored across discovered S3 buckets. Now we can move into creating a policy.
Step 2. Creating a Policy
Open Raven allows you to apply Policies to enforce your data security standards. This lets you both audit and monitor your cloud infrastructure for mismatches between data types and security configurations.
Policies comprise of as many or as few rules as you would like to include. Rules can be selected from our list of over 150 built-in rules, or can be custom created using our 'policy as code' rules editor.
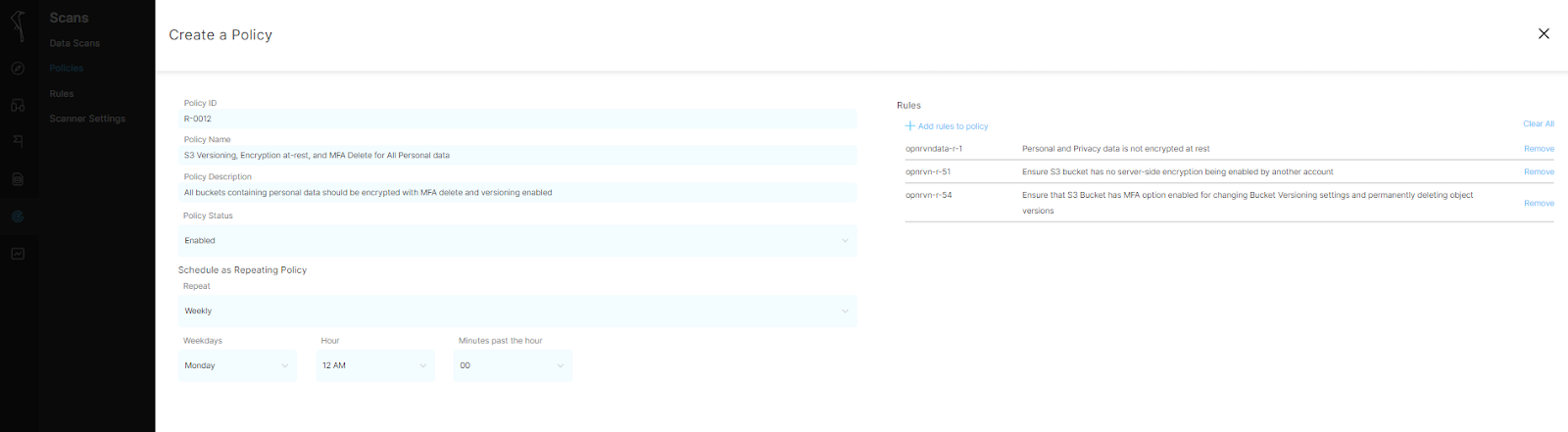
Create a new policy and give it a recognizable name: "S3 Versioning, Encryption, and MFA Delete for all Personal Data".
Select a schedule for this policy to run—once, daily, weekly, monthly.
Finally, search for and add the S3 bucket versioning, encryption, and MFA delete rules to the policy and save.
Now, Open Raven will scan your cloud for the data and configuration conditions specified in your policies. In the event that conditions are not met, a new record in Violations will be created that includes all necessary information to verify, assess, and prioritize next steps.
Step 3. Violations and Alerts, Your Way
When Violations are found, warning icons will appear on Maps and new records will be shown on the Policy Violations page, as seen below.

We recommend using our integration options, like Slack or Email, to route Violation alerts into your existing workflows. To do so, go to the Account Avatar, select Settings, Integrations, then select an option to have Alerts sent to Slack, email, or Webhooks and Eventbridge for more customized integrations.

Step 4. Quickly Resolve an Issue
Alerts include all the necessary information to quickly assess the situation and prioritize actions including: account ID, region, bucket(s), object(s), impacted sensitive data types, and counts.
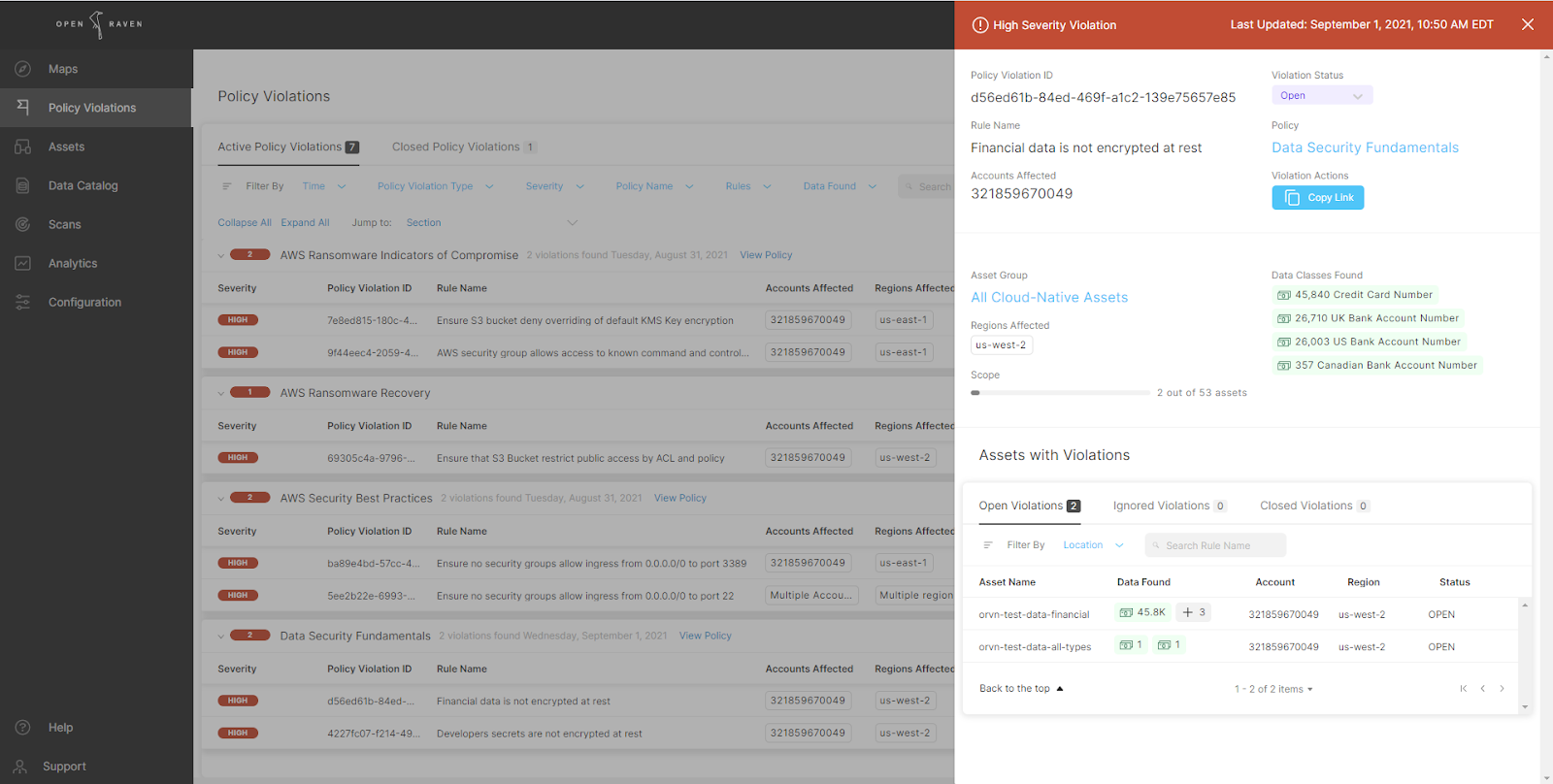
Use the deep links directly into the relevant part of the AWS Console (to an account, bucket, or object) to further investigate or resolve the issue.
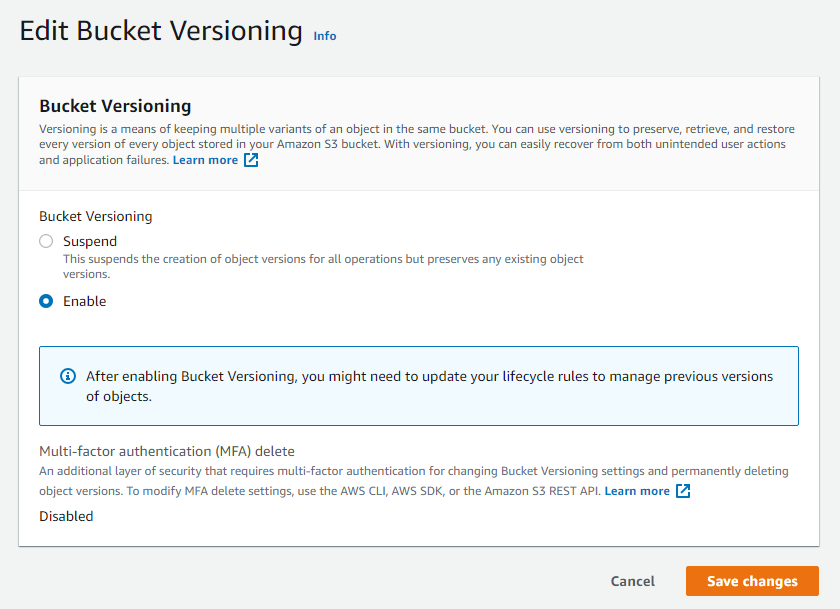
To enable S3 versioning for a bucket, use the deep link next to the bucket name in Open Raven to open the AWS console. From there, select Properties, locate Bucket Versioning, and select Edit. Change the setting to Enable, then save changes.
Configuring encryption for buckets can be done in a number of ways depending on the type of encryption. In short, there are server-side and client-side options to consider depending on the resource(s) being encrypted. These options can be configured via AWS S3 Console, REST APIs, SDKs, CLI, or CloudFormation.
To enable MFA Delete, you must use either the AWS Command Line Interface (CLI) or the API, which you can read about here.
Interested to see more? Schedule a demo with one of our security experts.